The Central Nervous System of Modern Cybersecurity: The Security Operation Center
In an era of relentless and sophisticated cyber threats, organizations require a centralized command hub for their defense strategies. This critical function is fulfilled by the Security Operation Center (SOC), a dedicated facility where an information security team continuously monitors and analyzes an organization's security posture. The SOC's mission is to prevent, detect, analyze, and respond to cybersecurity incidents. Its growing importance is reflected in market projections, which anticipate a steady compound annual growth rate of 8.2% through 2032. This expansion is significantly propelled by widespread cloud adoption and the prevalence of Bring Your Own Device (BYOD) policies, both of which expand the corporate attack surface and necessitate a robust, centralized security monitoring and response capability to protect sensitive data across diverse environments.
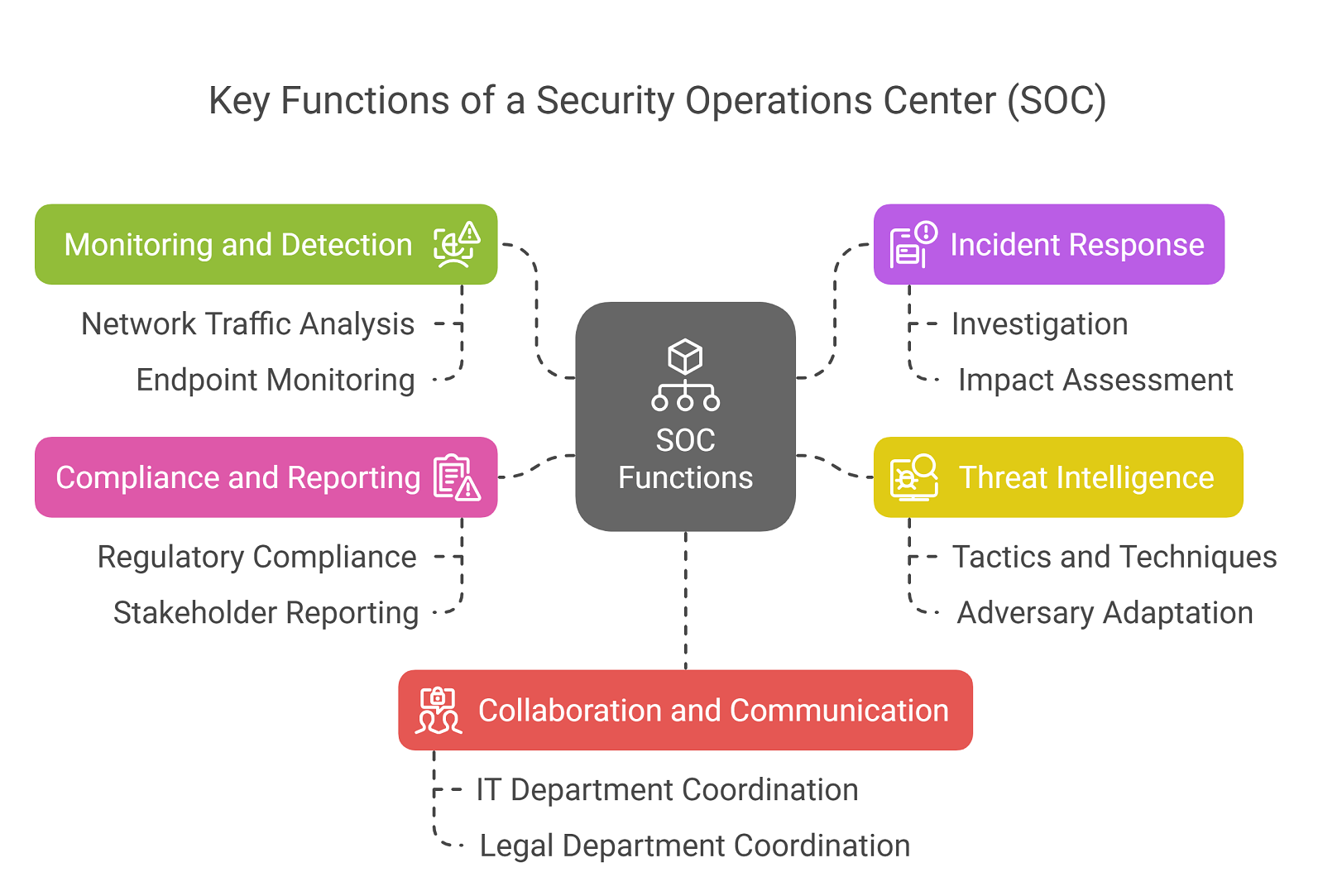
The effectiveness of a SOC is built upon a foundation of three core pillars: people, processes, and technology. The "people" component consists of highly skilled security analysts, engineers, and managers who work in tiered roles to handle incidents of varying severity. The "processes" are the well-defined playbooks and workflows that guide the team's response to different types of security events, ensuring consistency and efficiency. The "technology" pillar is the arsenal of tools the SOC uses, with Security Information and Event Management (SIEM) systems at the core. SIEMs aggregate and correlate log data from across the network, while other tools like Endpoint Detection and Response (EDR), threat intelligence platforms, and vulnerability scanners provide deeper visibility and context, creating a comprehensive security monitoring ecosystem.
Despite its critical role, building and maintaining an effective in-house SOC presents significant challenges. The most pressing issue is the global cybersecurity skills shortage, which makes it incredibly difficult and expensive to recruit and retain qualified analysts. Another major problem is "alert fatigue," where analysts are overwhelmed by a high volume of low-fidelity alerts, potentially causing them to miss genuine threats. Furthermore, the financial investment required for advanced security tools, coupled with the operational cost of maintaining a 24/7/365 monitoring capability, can be prohibitive for many small and medium-sized enterprises (SMEs), making it a resource-intensive undertaking that requires careful planning and substantial, ongoing investment.
Looking ahead, the evolution of the SOC is being driven by automation and the rise of managed services. To combat alert fatigue and improve efficiency, Security Orchestration, Automation, and Response (SOAR) platforms are becoming integral, automating routine tasks and orchestrating complex response workflows. For organizations unable to build their own SOC, the SOC-as-a-Service (SOCaaS) model offers a compelling alternative, providing access to enterprise-grade security monitoring and expertise on a subscription basis. This model democratizes access to advanced cybersecurity, allowing businesses of all sizes to achieve a mature security posture without the massive upfront investment, ensuring the SOC remains a vital component of defense strategies for years to come.
Explore Our Latest Trending Reports:
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Games
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness